Phishing Human Factors
Malicious communications, also known as phishing, are a serious problem to organizations and individuals world-wide. The Ponemon Institute in 2017 estimated phishing costs UK organizations an average of $2.01 million per incident. Phishing is also a common gateway to larger attacks, in 2019 alone 32% of data breaches started with a successful phishing attack (Verizon) making them particularly important to prevent.
The TULiPS lab is working on several lines of research around understanding the human-level impacts of phishing, challenges people face when trying to identify phishing, challenges organizations face in managing phishing, and tools to better support anti-phishing efforts.
Phishing awareness
While most people are aware that online scams exist that awareness is often not enough on its own to fully avoid falling for one. In order to accurately detect phishing users need to know how to assess the authenticity of an email and know what to do once they identify a potential attack. Phishing emails can be very scary and threaten to do things like kick a student out of the country due to visa issues or delete a valued online account. Just deleting such an email can also be terrifying for a user if they are not 100% sure that it is indeed a scam.
We reviewed the types of guidance companies, universities, and governments give to end users about how to detect and manage phishing across multiple countries [5]. We found that guidance has a very wide range both in terms of content and the specificity of the guidance. Some guidance is even contradictory such as guidance around spelling errors with some groups saying that spelling errors are an indication of phishing while others say that attackers are now good at fixing spelling and that it should not be used to judge a communication safe.
URL Reading
Reading a URL is one of the key abilities necessary for identifying malicious communications, but many people cannot accurately read a URL and predict where it will go. This happens for several reasons, URLs are naturally complex to read, visually identical characters can easily confuse a person, and for some URLs, such as shortened ones, it is physically impossible to predict the destination from simply reading the text due to redirection.
Managing phishing reports
Assuming that users are able to accurately detect phishing, they should really report it. But what happens to those reports? Often they have to pass through a process of manual labeling by Security Operations Center staff to determine if they are really phishing. Then key features have to be extracted to create rules that can be added to email and other filters. Needless to say, this process can take some time which is problematic.
In this project, we aim to better understand the workflows of the people who process phishing reports. What actions do they take? Who all is involved? All with the goal of making their job easier and more efficient.
Publications
- Faheem: Explaining URLs to people using a Slack bot [bibtex]
K. Althobaiti, K. Vaniea, S. Zheng; In Symposium on Digital Behaviour Intervention for Cyber Security. 2018. - Automatic phishing detection versus user training, Is there a middle ground using XAI? [bibtex]
S. Albakry, K. Vaniea; In Proceedings of the SICSA Workshop on Reasoning, Learning and Explainability. 2018. - A Review of Human-and Computer-Facing URL Phishing Features [bibtex]
K. Althobaiti, G. Rummani, K. Vaniea; In IEEE European Symposium on Security and Privacy Workshops (EuroSPW). 2019. - What is this URL's Destination? Empirical Evaluation of Users' URL Reading [bibtex]
S.S. Albakry, K. Vaniea, M.K. Wolters; In Proceedings of the 2020 CHI Conference on Human Factors in Computing Systems. 2020. - Analysis of publicly available anti-phishing webpages: contradicting information, lack of concrete advice and very narrow attack vector [bibtex]
M. Mossano, K. Vaniea, L. Aldag, R. Düzgün, P. Mayer, M. Volkamer; In Proceedings of the 5th IEEE European Workshop on Usable Security (EuroUSEC). 2020. - I Don't Need an Expert! Making URL Phishing Features Human Comprehensible [bibtex]
K. Althobaiti, N. Meng, K. Vaniea; In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. 2021. - A Case Study of Phishing Incident Response in an Educational Organization [bibtex]
K. Althobaiti, A. Jenkins, K. Vaniea; In Proceedings of the ACM Conference on Computer Supported Cooperative Work and Social Computing. 2021. - PhishED: Automated contextual feedback for reporting phishing [bibtex]
A. Jenkins, N. Kokciyan, K. Vaniea; In Proceedings of the Symposium on Usable Privacy and Security Poster Track. 2022. - Context-based Clustering to Mitigate Phishing Attacks [bibtex]
T. Saka, K. Vaniea, N. Kokciyan; In Proceedings of the 15th ACM Workshop on Artificial Intelligence and Security (AISec 2022). 2022. - ``{I} didn't click'': What users say when reporting phishing [bibtex]
N. Pilavakis, A. Jenkins, N. Kokciyan, K. Vaniea; In Proceedings of the Symposium on Usable Privacy and Security (USEC'23). 2023.
People
- Sara S. Albakry
- Kholoud Althobaiti
- Tarini Saka
- Nadin Kokciyan
- Kami Vaniea
- Maria Wolters
Funding
Research and projects here are partially funded by the following groups:- Google Faculty Award
Related Student Projects
The following are related projects completed by interns, undergraduate, and masters students.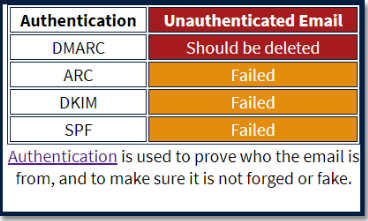
Automatically Generating Contextualised Responses to Phishing Reports
Sean Strain
Supervisors: Kami Vaniea, Adam Jenkins
I propose a novel system that respons to reports of email phishing with contextualised information and advice. The first year of the project analyses a given email for a range of phishing indicators and dynaically generates a set of features that can be used to create a friendly and educational response. The second year of the project involved creating a simulated inbox interface which showed the output of the system in a realistic setting. A study with 22 participants was then used to evaluate how users interacted with the system and how much it helped users identify and learn about phishing.
Correlating Information on Email to Help the User Receive Better Understanding on Identifying Phishing Email
Isa Albashar
Supervisor: Kami Vaniea
Phishing is a popular method to obtain sensitive data from users such as login passwords. Unfortunately automatic detection methods, while quite accurate, are not 100%, so some phishing emails appear in user inboxes. Users are recommended to report such email, but they are unlikely to get a quick response if they do. In this project I create a prototype for an auto responder system that gives a summary of email analysis which consists of the email features identified and has a friendly explaination.

Cyber Security Game: An education game to teach non-technical employees about phishing emails
Wenning Jiang
Supervisor: Kami Vaniea
Phishing emails are one of the most dangerous attacks in recent years, lurking in email inboxes for the unwary. Serious games present a potential way to teach users about phishing in a more fun environment. This project designed a progressive game where the difficultly raises in levels. Thereby increasing the challenge as the player progresses.

Analysis of phishing emails for construction of auto-generated advice
Daria Popova
Supervisor: Kami Vaniea
Phishing is an attack that exploits how people interpret email content, in paricular, exploiting: fear of scarcity, authority, guilt, and gullibility. I perform an analysis of an email dataset using deep neural networks and automated classifiers in an effort to provide users with useful predicted guidance.
The Impact of Cross-National Differences on Phishing Email Detection Ability
Mingyang Dong
Supervisor: Kami Vaniea
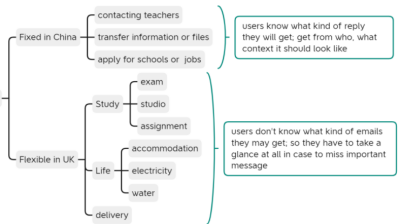
Phishing is a crime that employs both social engineering and technical methods to steal sensitive personal information. People who relocate from a region or culture where communication is done differently can be particularly vulnerable to phishing. One of the most common phishing avoidance advice is to see if the message `looks odd' which is easy for someone who is established in their community or job, but is very challenging for someone who just relocated. This project aims to better understand the phishing-related challenges faced by students who relocated from China to the UK for their studies. We find that University communication in China is normally done over communication channels that verify the sender's identity, like WeChat. Whereas similar communication in the UK is over email which is not properly authenticated. These differences cause challenges for international students.
Designing an Autoresponder for Phishing Email Reports
Zeyu Zhang
Supervisor: Kami Vaniea
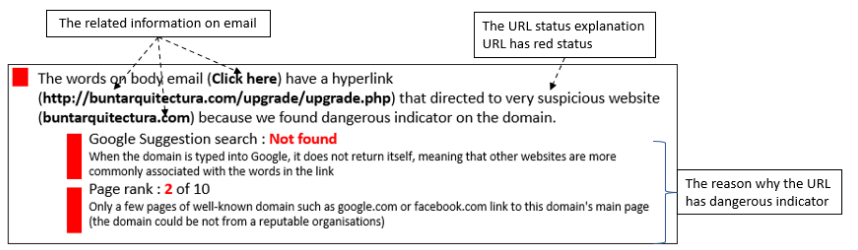
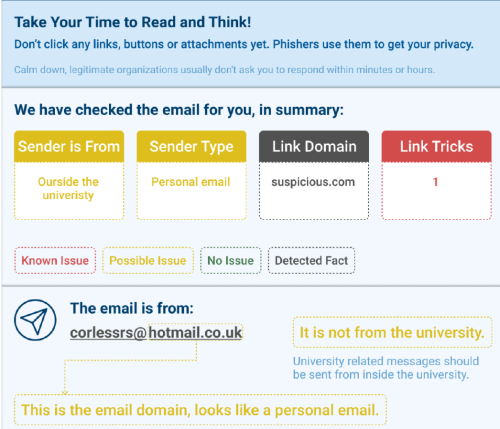
Nowadays, it is common for organizations to support their members recognizing phishing by encouraging them to report any suspicious emails. However, as a kind of human assistance, not every inquirer can be responded in minutes, while speed can matter a lot because phishers often press their targets to make immediate decisions by injecting a sense of urgency. In addition, as the help desk workers might not be phishing experts either, their feedback is not always helpful that it might be very general but not customized to a certain reported email. Therefore, I designed an automatic responder for phishing email reports, which is technical feasible to implement to return immediate feedback to the inquirer. According to the design, the responder can automatically parse the reported emails and notify the findings through specific colors and texts, ranging from safe to dangerous. This solution combines the human autonomous decision and more reliable automated detection methods, which cover a wider range of phishing features compared to most user-support tools, including email headers, internal URLs, and email body. Also it focuses on explaining those features to ordinary users. Through user evaluation with 6 non-experts participants, the feedback is demonstrated to be generally comprehensible, helpful and friendly.
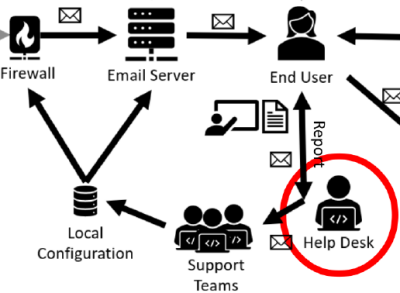
Clustering Phishing Emails to Help the Helpdesk
George Gilligan
Supervisors: Kami Vaniea, Kholoud Althobaiti
In this project I unpack, decode, parse, vectorise and cluster malicious emails, with the intention of grouping them into phishing campaigns. The work is motivated by a desire to automate the work of an organisation helpdesk, who are currently consigned to manual labeling of each phishing email individually. The results show promise that phishing campaings can be clustered.
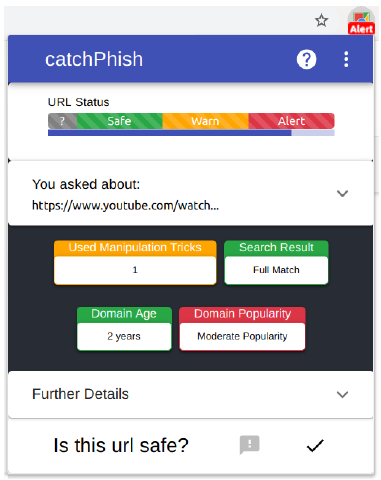
CatchPhish: A URL and Anti-Phishing Research Platform
Stephen Waddell
Supervisors: Kami Vaniea, Kholoud Althobaiti
CatchPhish Phishing Learning and Detection Tool is a browser extension and cloud analysis system designed to improve phishing detection by training users to detect malicious URLs. This work represents a novel contribution to anti-phishing research by combining both passive indicators and active warnings into a system which actively aims to train users.
By leveraging Google cloud technologies, a URL analysis server supports the extension with the ability to scalably analyse URLs with a high degree of accuracy. It is built with a Microservices-based architecture deployed on Google App Engine, which integrates a heuristic algorithm with numerous data sources and 46 distinct heuristics, to facilitate the system's analysis requirements.
The research is underpinned by user studies to gather requirements about what solutions would most benefit users. The evaluation of the overall system illustrates the utility of CatchPhish as a versatile research platform for experimenting with different anti-phishing approaches.

Analysing Online Anti-Fraud Advice to Identify Common Anti-Phishing Instructions and Assumptions
Mattia Mossano
Supervisor: Kami Vaniea
There is a wide variety of anti-phishing advice available through many organizations such as banks, universities, law enforcement, and consumer advacacy groups. In this work, I collect advice from 94 web pages across 9 countries. I find that the advice given to users is disorganized with different advice given by different groups and sometimes the same group offering different advice for differenty entities.

Web-based tool for estimating security training approaches for security decision-makers
Nan Sheng
Supervisor: Kami Vaniea
Cyber security has been a concern for organizations because it can lead to large financial loss. The premise of this project is that the CISO realizes the improtance of cyber security training and is trying to find a suitable training approach for the staff. This project collects essential information about training approaches from academic papers and training companies such as methodology, charateristic, effectiveness, cost and commercial training products. The goal is to help someone like a CISO select a suitable training approache for the staff.
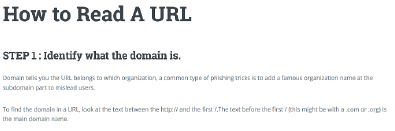
Empirical Evaluation of Users' Ability to Read URLs With and Without a Support Website
Xinding Wang
Supervisor: Kami Vaniea
Reading a URL unaided is challenging. This project had two goals:
1) Determine if people in China and Europe read URLs differently.
2) Build a website that parses and explains a URL to someone in both English and Chinese.

Faheem: Real-time Slack Bot URL Explainer Assists Users in Overcoming Phishing
Kholoud Althobaiti
Supervisors: Stuart Anderson, Kami Vaniea
People have difficulty understanding URLs which makes it harder for them to decide what links are safe to click on or identify potential privacy issues. Faheem is a Slack chat bot designed to help users understand a URL through an interactive discussion with the bot.
