Developer Centered Security and Privacy
The overall goal of this project is to develop a usable SSL/TLS API by studying how developers with limited security background approach adding encryption to their projects, followed by identifying common sources of error, and then iteratively designing an API that supports adding security as part of the developer's typical work model.
SSL/TLS is used to encrypt communication between devices on the internet, but many developers make errors when attempting to incorporate these libraries into their projects, leading to serious security problems such as data leakage and potential compromise of devices. It is estimated that as many as 88% of Android apps contain at least one cryptographic API usage mistake, e.g., using constants for keys, salt, seeds, or choosing the wrong encryption mode [1].
Just like any other human computer interface, APIs need to be designed to be usable, minimize accidental error, and generally support the workflow of users. When these principles are not taken into account, it becomes easy for even highly skilled developers to make mistakes. While several HCI methods exist for exploring API usability and creating new API designs, in general there have been few attempts to apply them to security libraries.
[1] Manuel Egele, David Brumley, Yanick Fratantonio, and Christopher Kruegel. An empirical study of cryptographic misuse in Android applications. In Proc. ACM CCS’13, pages 73–84. ACM, 2013.Publications
- "I Don't Know Too Much About It": On the Security Mindsets of Computer Science Students [bibtex]
M. Tahaei, A. Jenkins, K. Vaniea, M.K. Wolters; In Workshop on Socio-Technical Aspects in SecuriTy (STAST). 2019. - A Survey on Developer-Centred Security [bibtex]
M. Tahaei, K. Vaniea; In European Workshop on Usable Security (EuroUSEC). 2019. - Understanding Privacy-Related Questions on Stack Overflow [bibtex]
M. Tahaei, K. Vaniea, N. Saphra; In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems. 2020. - Security Notifications in Static Analysis Tools: Developers' Attitudes, Comprehension, and Ability to Act on Them [bibtex]
M. Tahaei, K. Vaniea, K. Beznosov, M.K. Wolters; In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. 2021. - Privacy Champions in Software Teams: Understanding Their Motivations, Strategies, and Challenges [bibtex]
M. Tahaei, A. Frik, K. Vaniea; In Proceedings of the 2021 CHI Conference on Human Factors in Computing Systems. 2021. - ``Developers are Responsible'': What Ad Networks Tell Developers About Privacy [bibtex]
M. Tahaei, K. Vaniea; In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems Late Breaking Work. 2021. - Code-Level Dark Patterns: Exploring Ad~Networks' Misleading Code Samples with Negative Consequences for Users [bibtex]
M. Tahaei, K. Vaniea; In ``What Can CHI Do About Dark Patterns?'' Workshop at CHI Conference on Human Factors in Computing Systems (CHI '21). 2021. - Deciding on Personalized Ads: Nudging Developers About User Privacy [bibtex]
M. Tahaei, A. Frik, K. Vaniea; In Symposium On Usable Privacy and Security (SOUPS). 2021. - Understanding Privacy-Related Advice on Stack Overflow [bibtex]
M. Tahaei, T. Li, K. Vaniea; In Proceedings on Privacy Enhancing Technologies. 2022. - Recruiting Participants with Programming Skills: A Comparison of Four Crowdsourcing Platforms and a CS Student Mailing List [bibtex]
M. Tahaei, K. Vaniea; In Proceedings of the SIGCHI Conference on Human Factors in Computing Systems. 2022. - Lessons Learned From Recruiting Participants With Programming Skills for Empirical Privacy and Security Studies [bibtex]
M. Tahaei, K. Vaniea; In 1st International Workshop on Recruiting Participants for Empirical Software Engineering (RoPES'22). 2022. - Embedding Privacy Into Design Through Software Developers: Challenges and Solutions [bibtex]
M. Tahaei, K. Vaniea, A. Rashid; In IEEE Security & Privacy. 2023.
People
Funding
Research and projects here are partially funded by the following groups:- Microsoft Research Studentship Award
Additional Resources
All the additional resources for the publications such as interview scripts, datasets, and presentations are available in our wiki page.
Related Student Projects
The following are projects completed by interns, undergraduate, and masters students related to the project.
Usability Analysis and Improvement of Two Cryptographic Prototyping Frameworks
Ma Qing Gao
Supervisor: Markulf Kohlweiss
Cryptography schemes can be the core solution for ensuring computer security. This project focuses on conducting two usability lab study to evaluate the usability of two existing. This project focuses on conducting two usability lab study to evaluate the usability of two existing cryptographic prototyping frameworks, which are the three existing Python cryptography programming libraries: Charm, Petlib and Bplib. The final outcomes of this thesis were: (1) giving the weakness and improvement suggestion of the documentation and error respond of these libraries. (2) identify the syntax of which library is more acceptable and understandable by cryptographers.
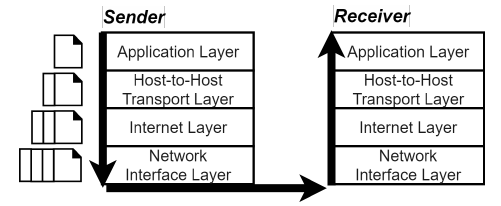
Putting the 'S' in HTTPS: Automatically Fixing Insecure HTTP and Flawed HTTPS Connections in Android
Vesko Stefanov
Supervisor: Kami Vaniea
Cryptographic solutions like HTTPS protect information in transit, but only if they are used correctly by developers. In this project, I develop an early prototype of an Android application which checks all outgoing connections from the device and where possible auto-upgrades them to HTTPS connections. I also test how feasible it is to auto-upgrade HTTP connections in terms of the ability of remote servers to accept the upgraded connections.

Encrypt me if you can: Helping developers add Transport Layer Security to Android applications
Dimple Gulrajani
Supervisor: Kami Vaniea
An alarming number of mobile applications on the Google Play store do not encrypt their communications leaving them open to Man In The Middle attacks. This thesis analyzes why this is the case and presents a new tutorial to help developers correctly use TLS.
